A Comprehensive Guide to Understanding and Implementing MOS: The Management Operating System
MOS, or Management Operating System, is a bunch of tools, behaviors, and meetings used to organize your procedure for delivering results. A Management Operating system is responsible for following, performing, checking, and acting on a plan to improve the cycle to obtain control and improve the patching process performance. Patching can be a time-consuming and automated patch management process that allows you to reduce errors and save time.
Operating system management is an individual task that refers to UNIX literature as the system administrator. A few system administrators are precise enough to be called an administration. Related guides are available to help system administrators with their innumerable duties.
OS is a particular version of the system management support to enhance security and integrity and to facilitate ease of use.
-
- What is the patch management lifecycle?
- Why do we need patch management?
- What are the different types of patches?
- The patch management process
- Classify the risk:
- Entrenching Patch Management into Vulnerability Management Measures:
- Vulnerability Patching:
- Vulnerability and Patch Management Process
- Vulnerability and Patch Management Software:
What is the patch management lifecycle?
Patch management is a subset of system administration that includes obtaining and testing patches, identifying code changes, testing and applying patches, adding features, fixing faults, and closing security gaps. Updates for software and operating systems (OS) are the fixes to fix security flaws in a program or product.
Patch management is essential for staying up to date with newly released patches, deciding which missing patches are needed for specific software and devices, testing the patches, ensuring they have been properly installed, and documenting the whole process.
Why do we need patch management?
Implementing patch management is advised by well-known frameworks and regulations, such as ISO 27001, PCI DSS, and NIST.
Patch management is significant for the following fundamental causes:
-
Security:
Patch management sets vulnerabilities in applications and software exposed to cyber-attacks, supporting your institution to decrease its security risk. If computerized options are functional, the Cybersecurity and Infrastructure Security Agency (CISA) suggests taking advantage of them.
-
System uptime:
Patch management ensures your applications and software are maintained up-to-date and operate smoothly, verifying system uptime.
-
Compliance:
With the persistent ridge in cyber-attacks, institutions are often mandated by regulatory bodies to keep a particular level of subordination. Patch management is a vital piece of clinging to compliance standards.
-
Feature improvements:
Patch management can move additional software bug fixes to incorporate feature updates. Patches can be compulsory to ensure you have the most delinquent and significant derivative offers. Along with measures are marks or key performance indicators (KPIs). These are manipulated to articulate the level of performance you are attempting to achieve.
What are the different types of patches?
There are numerous classes of patches:
-
Software patches:
These Patches fix existing vulnerabilities or bugs as they are seen after a portion of software or hardware has been terminated.
-
Hotfix:
A hotfix patch is developed to improve a specific problem. Unlike regular patches, these hotfixes are produced and released as soon as practicable to restrict the impacts of a software issue.
-
Point Release or Dot Release:
A point release, or a dot release, is a small or relatively minor update planned to fix software errors or defects without adding features.
-
Maintenance Release:
Incremental updates between service packs or software versions to fix multiple outstanding issues.
-
Security Patches:
A security patch is a change applied to an asset to correct the weakness described by a vulnerability.
-
Service Pack (SP) or Feature Pack (FP):
Major patches include a supply of updates, fixes, or feature enhancements to a software program delivered in the state of a single installable package. These usually designate many notable issues and typically possess all the patches, hotfixes, supervision, and security patches released before the service pack.
-
Unofficial Patches:
These patches are produced by a third party or a user community, considerably because of a deficiency of support from the actual software developer, for example, the software company went out of business or when a software derivative has achieved its specified end-of-life.
-
Monkey Patches or Guerrilla Patches:
Alike unofficial patches, a monkey patch, also known as a guerrilla patch, is an update designed to develop or modify the conduct of a software product or plugin or locally without transforming the source code.
The patch management process
It would be a poor technique to install new patches the second they evolve available for all supports in the organization's merchandise without thinking about the consequence. Instead, a more strategic guideline should be endured.
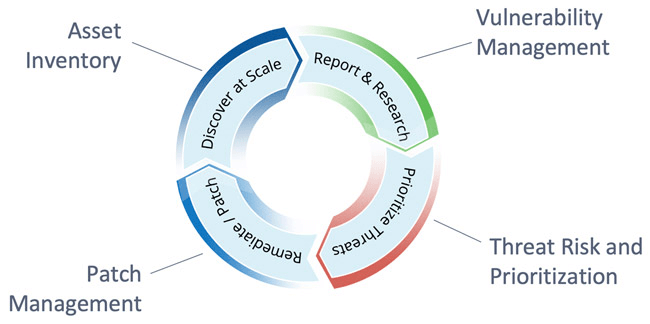
Patch management should be executed with a careful, security-focused, cost-effective organizational procedure. A centralized patch management server accomplishes more than automating patch management; it also offers the association control over the patch management process. Here are some key steps to patch management:
Step 1 - Develop an up-to-date:
Observe what assets exist in the ecosystem, whether monthly or quarterly, through this step. Through active asset management, you will have an informed view of version types, existing IP addresses, and their organizational owners and geographic locations.
Step 2 - Devise a plan:
Although devising a plan is difficult, standardizing your asset inventory completes patching more instantaneously and efficiently. You will be required to regularise your assets to a manageable numeral to accelerate your remediation methodology as new patches are released. This will support both you and the technology teams.
Step 3 - Make a list of all security controls:
Keep track of your antivirus, firewalls, and vulnerability management tool. You should know what they’re protecting, where these are sitting, and which assets are linked with them.
Step 4 - Compare reported vulnerabilities:
Assessing which vulnerabilities exist for which assets in your ecosystem will help you understand your security posture and risk as an organization using your vulnerability management tool.
Classify the risk:
Using vulnerability management tools, you can effortlessly manage which assets you consider critical to your organization and prioritize what needs to be treated accordingly.
-
TEST:
Apply the patches to a representative sample of assets in your lab. Stress test the patch testing the machines to ensure that the patches will not create any issues in the production environment.
-
Apply the patches:
Start patching once you have decided what to prioritize to decrease the environmental risk. More advanced vulnerability management tools also offer the ability to automate the time-consuming pieces of the patching process.
-
Track your progress:
Reassess your assets to guarantee patching was successful.
Entrenching Patch Management into Vulnerability Management Measures:
Patch management is critical to every vulnerability management program. Regardless, keeping a uniform approach to patch management doesn’t always suggest smashing a fix on everything in sight.
The phrase “patch management” and “vulnerability management” are interchangeably used, though it is necessary to apprehend the dissimilarity. Though patch management and vulnerability management aim to identify and mitigate threats, patch management is limited in scope. To ensure a comprehensive security posture, organizations should holistically implement vulnerability and patch management best practices. This will provide the necessary insight to make informed decisions and maximize the effectiveness of security efforts. Vulnerability management constantly prioritizes, identifies, reports, and remediates security vulnerabilities in systems and the software that executes them.
A critical component of patch management is vulnerability management, as it is a piece of the puzzle to address security vulnerabilities. Following steps are required to implant patch management in the vulnerability management program.:
-
Establish asset management:
Your capacity to lessen the risk is only as valuable as your environmental visibility. Suppose you are looking for a patch management solution that can offer all the security features above. In that case, many tools offer an efficient solution with powerful features to keep your network patched with the most delinquent patch updates.
-
Prioritize vulnerabilities.
With restricted time and resources and an ever-changing hazard landscape, it’s ideological to think you can resolve every vulnerability as it appears. Therefore, prioritization is one of the most critical systems of vulnerability management.
-
Remediate vulnerabilities to reduce risk
Recognizing and prioritizing vulnerabilities is necessary, but you’re not lowering risk unless you remediate the problems.
-
Measure the success of your vulnerability management program:
No matter how many flowery characteristics a vulnerability management solution holds, it’s worth the asset if it satisfies your organization’s distinctive demands and adds significance to you and your group.
-
Develop partnerships and support
When something drives faulty, you want to know you have a group of individuals you can depend on to aid troubleshooting.
Vulnerability Patching:
Protecting security in business environments is essential for some reasons, not least the risk of a data security breach or service trouble. Using enterprise software and associated add-ons can yield vulnerabilities that let malicious actors enter your IT environment. Modernizing your systems regularly is significant, and patching vulnerabilities are compulsory to ensure “gaps” are protected. The patching process can sometimes be complicated, as with multiple machines and numerous applications, you must ensure everything is updated. Regardless, patching and editing at inappropriate times can slow down services and applications, eventually affecting your end-user adventure.
Vulnerability patching is stemming your software, applications, and network components for vulnerabilities that could permit a malicious user to access your system and provoke damage. You could uncover your association with a vulnerability when you have a new installation, update, or download.
Vulnerability and Patch Management Process
It’s essential to have a vulnerability and patch management policy surrounding the devices and software you had on your web when they were last patched, a database of available vulnerabilities, a patching schedule, and more. Using a patch management policy across software vendors and the association can keep systems secure.
For Windows, the vulnerability patch management process starts with WSUS and SCCM. WSUS stands for "Windows Server Update Services", the complimentary vulnerability and patch management tool that arrives with Windows. SCCM is the "System Center Configuration Manager" and is a paid tool. You can also establish Windows systems. Both mechanisms are valuable when handling Windows machines in a large enterprise, especially workstations and Windows servers.
These instruments are a good beginning for your patching and vulnerability management practice, but their functionality is restricted. Patching tools can produce what WSUS and SCCM propose, which is imperative if you operate many third-party applications or employ a cross of both Windows OS and non-Windows devices on your network. For instance, if your network is moderately available and you have a lot of portable devices connecting seldom, you may be trading with a group of operating systems and machines that ought to be covered.
However, you must maintain a clear patch management plan for your tool. Patching and vulnerability management are continuous processes, so you shouldn’t regularly roll out patches. Deploying and managing patches by procedure across an entire enterprise can generate significant slowdowns for applications and services, eventually affecting end users. Using a tool to assist you schedule and automating patching in a way suited for your enterprise is more beneficial. Once the patch deployment happens, statements on the status of the automated patch management tasks are revised. With an automated Patch Management solution, each enterprise is provided to update its endpoints with the most delinquent patches irrespective of what OS they run and where they are discovered.
Vulnerability and Patch Management Software:
The right patch management software creates all the difference for a thriving vulnerability and patch management process. As mentioned, WSUS is already a feature of Windows systems, and you can also spend for Microsft SCCM. Yet, in multiple issues, you need to look at third-party tools to sustain critical patches for the systems you already own through Windows. How to pick the right patch management software? How do you understand which patch management software is most profitable for your organization? The request differs from business to business. However, there are common periodic characteristics that most organizations peek for in patch management software
A suitable prospect to examine is SolarWinds Patch Manager, which can be exploited for patching servers, workstations, and applications. It also combines well with Microsoft SCCM and WSUS, so you can utilize it to sustain any tools you are operating. Patch Management software supplies a forceful patch management plan, with patch management tools to help you notice which servers and workstations must be patched. In addition, it contains characteristics to help you build deploy patches or patch deployment packages, such as targeting a respective operating system or containing devices exclusively within a specific IP range.
Frequently Asked Questions
What is an operating system?
An OS manages computer hardware and software resources and provides standard services for computer programs. It is the backbone of any computer system, enabling communication between hardware components and allowing applications to run on the machine.
What is OS management?
The process of controlling and maintaining the system to ensure it functions properly. This includes installing updates and patches, monitoring performance, installing patches, managing storage, and configuring security settings.
What are some standard operating systems?
Windows, macOS, Linux, iOS, and Android. Windows and macOS are desktop operating systems, while servers use Linux more often. iOS and Android are mobile operating systems used on smartphones and tablets.
What skills are required for systems management?
Skills required for operating systems management include knowledge of the specific operating system being managed, knowledge of computer hardware, problem-solving skills, critical thinking skills, and strong communication skills.
What are tools and business processes used for systems management?
Tools used for operational systems management include monitoring and management software programs, system configuration tools, patch management tools, and security software. Examples of popular tools include Microsoft System Center Configuration Manager, SolarWinds Patch Manager, and Norton Security.
Why is OS systems management necessary?
It is essential for several reasons. Firstly, it ensures that the system functions correctly, ensuring that applications and software can run smoothly. Secondly, it helps protect against various security risks and threats and secure sensitive data. Finally, it can help to optimize system performance and prevent downtime.